NSO isn’t the Only One: Candiru, an Israeli Company Offering Spyware Systems for Oppressive Regimes

Throughout the last few days, Arab and international media outlets have run stories of a new leak concerning NSO Group, one of the most well known Israeli companies active in the fields of surveillance and spying. NSO develops Pegasos, one of the most well known tools used by oppressive governments and regimes for spying on and monitoring activists, human rights defenders, and political dissidents.
Pegassos is counted among the advanced spyware, as it enables political regimes using it of hacking into smartphones gaining access to photos, videos, text messages, and communications. NSO also uses zero-day attack approach for hacking into smartphones, computers, and servers, extracting data out of them.
Read: How to Protect Your Data from Israeli NSO’s Surveillance Attacks? – SMEX’s website
Israel is home for tens of mercenary electronic spying and surveillance companies. Usually, such companies work publicly boasting about their services. NSO, isn’t the only one. There is also Candiru. Established in 2014, Candiru was able to keep a low profile for most of its years in business, by observing full secrecy. It doesn’t even have a website, thus there is only very limited information about it.
What is Candiru?
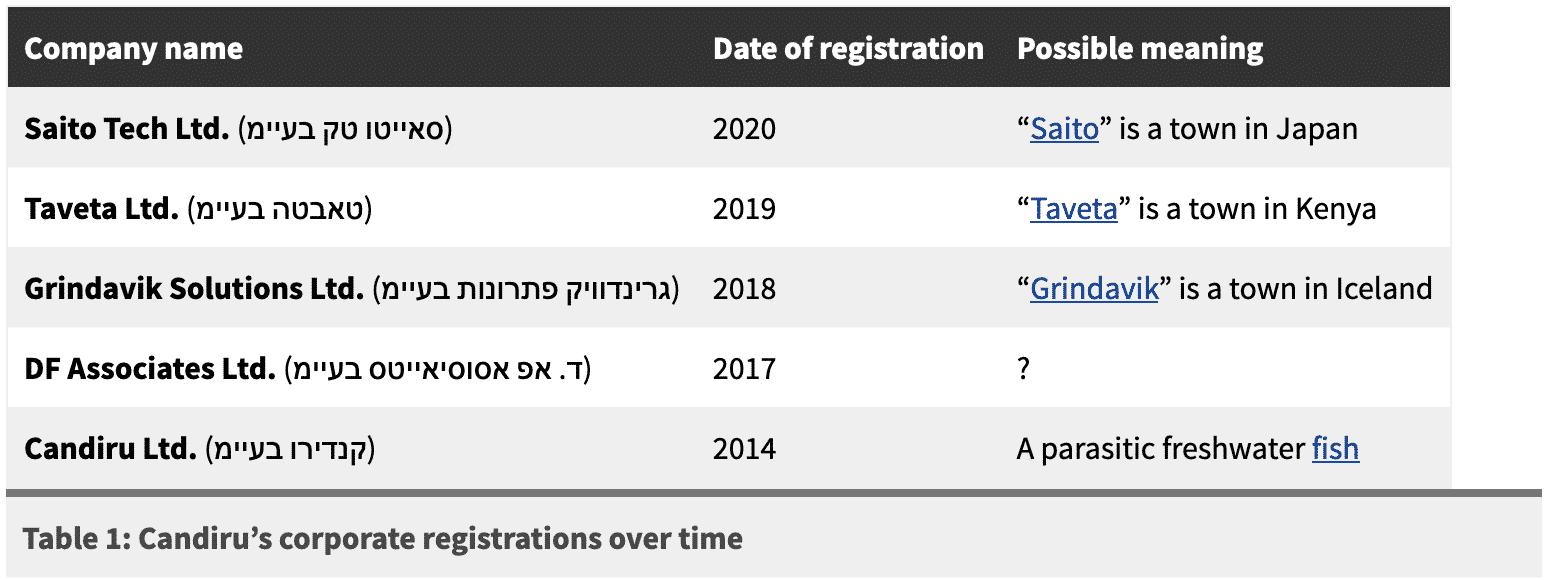
Candiru is used extensively by the Israeli Defense Forces (IDF) intelligence corps (Unit 8200). Candiru employees usually are paid generously, earning 20K to 28K US Dollars per month. The company imposes strict policy of secrecy internally. None of its employees may publish or update personal files on LinkedIn. They sign strict confidentiality agreements. On July,15th Citizen Lab published a report about Candiru and the spyware it develops. According to this report, the company makes a lot of effort to keep its operations, infrastructure, and the identities of its employees unknown. It hides behind the names of several companies. Throughout the last few years, the company changed its name several times, and the following table lists some of the names it used over the years.
What are the spying abilities of Candiru’s systems?
Candiru sells its products to oppressive governments, providing them with software for spying on computers, smartphones, and cloud computing services. The company says that its spying services “can’t be traced”.
A document leaked by “The Marker” (an Israeli magazine) about Candiru, describes the technical spying abilities provided by the company’s products. According to this document, the company sells a full intelligence system that works as an advance platform dedicated to hacking into computers, smartphones, and networks by exploiting security holes within the systems.
Candiru’s platform manages all hacking stages, starting with installing the hacking software on target devices, up to data and information extraction, which makes the platform highly dangerous. The hacker can determine all the networks communicated by the target, including the Internet, social networks, and email services. Additionally, the hacker gains large control power, allowing him to extract data and take control of the devices.
The company also claims that it can infiltrate devices using Windows, iOS, or Android. The Candiru system might be one of the most sophisticated software applications, given its high capabilities for infiltration.
Candiru uses a number of digital attack approaches to implant spyware on the target device, such as:
- A phishing link that automatically installs a malware.
- A Microsoft Office document that includes malware.
- Man-in-the-Middle attack, which an attack that depends on intercepting the hacked device data.
- Using the Shelock malware for targeting Windows, iOS, and Android devices.
As mentioned before, Candiru can infiltrate Windows, iOS, and Android systems. As a demonstration of the technical abilities provided by the Candiru spying platform, the Citizen Lab report mentions that the platform can hack into the devices using the Windows OS, carrying out its attacks through any browser, or by sending a phishing document to the target. After infiltrating the target device, the spyware can access the contents of many applications, such as Skype, Outlook, Telegram, Facebook, and others. It also can record all passwords, control the microphone, and camera, and determine geographic location.
Similarly, the spyware access data of smartphones (iPhones and Android), collecting communication records, calendar, and location, in addition to the ability to record phone calls. Concerning Android devices in particular, it is obvious that the company has a wide experience hacking into devices produced by the Korean Samsung. It seems that the cost of development is so high, as the leaked document indicates that the cost of purchasing Candiru platform and system is about 17 millions Euros, at least. It may cost up to 30 millions Euros, in addition to annually renewed subscription and extra fees for updates and upgrades.
Who are Candiru’s clients?
Based on several news reports, and the Citizen Lab report published recently, some of the most prominent clients of Candiru are the Arab regimes especially gulf countries, like the United Arab Emirates, and the Kingdom of Saudi Arabia. There have also been news reports of an investment relationship between Candiru and a Qatari company. It was revealed in 2019 that both Uzbekistan and Singapore have used the company’s spying services.
Who was targeted by Candiru, and how?
Commenting on the Citizen Lab report, Microsoft said that persons targeted with “accurate attacks” by spyware, were based in the Palestinian Territories, Israel, Iran, Lebanon, Yemen, Spain, UK, Turkey, Armenia, and Singapore. The targeted include human rights defenders, political dissidents, journalists, and political activists.
Citizen Lab researchers were able to determine more than 750 websites connected to Candiru’s spyware infrastructure. Many of the website names were similar to advocacy organizations websites, like Amnesty, Black Lives Matter, and other entities of civil society nature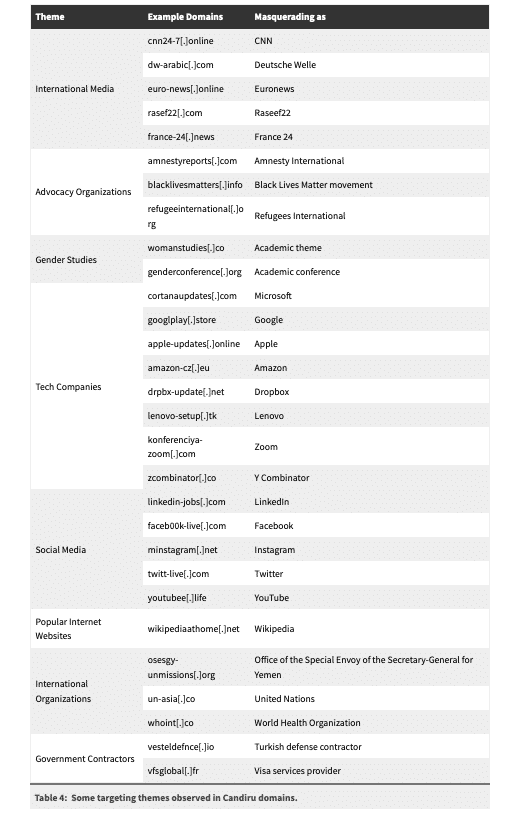
Technology companies stand over Candiru or NSO
In the end of 2020, a group of technology companies filed a memo supporting a lawsuit by WhatsApp against NSO, accusing the company of using unrevealed security hole in the chat application to hack into at least 1400 devices, some of them belong to journalists and human rights activists. Among these companies are Google, and Microsoft (including its subsidiaries LinkedIn and GitHub), Cisco, VMware, and Facebook.
After revealing Candiru’s infrastructure, Microsoft said that it blocked tools developed by the Israeli company, and managed to fix holes into its operating system exploited by the Candiru’s spyware.
Also, Google issued patches fixing 8 holes for its browser “Google Chrome”. It is believed that these updates are related to holes exploited by the Israeli company.
How can we protect ourselves against these software?
Generally speaking, we cant offer advice guaranteeing the protection of our devices against Zero-day attacks, but there are some procedures that can be taken for minimizing damage and leak of information.
- SMEX, a Lebanese organization concerned with defending digital rights, has published recommendations that may provide some security and protection. You can find these recommendations via: How To Protect Your Data From Israeli NSO’s Surveillance Attacks?
- Ali Al-Sebaei, a researcher and digital security expert has published a thread of tweets providing advice for digital security, which you can find via this link.
- Masaar- Technology and Law Community, has published a guide for Privacy and Security Options in Smartphones (Android and iOS), which you can find via this link.
- Masaar- Technology and Law Community, has published a guide for Privacy in Instant Messaging Applications, which you can find via this link.
- You can also read about How to Choose Secure Smartphone Applications? via this link.
